Microsoft just revealed the next iteration of Windows OS. Officially called Windows 11, Microsoft claims that they have completely redesigned the entire user experience with fresh new design elements like animations, icons, fonts, and much more from the ground up.
But all of that excitement slowly started turning into a disappointment, and in some cases, even frustration. Why, you wonder? It’s because when Microsoft released the system requirements for their shiny new version of Windows, they mentioned two key specs that were a must-have for running the upcoming release. They were Secure Boot and TPM 2.0, which couldn’t be found on even some of the latest products either from Microsoft themselves.
Related: Enable TPM 2.0 | Bypass TPM 2.0 requirement
Up until now, Windows versions starting from 8 till 10 could all be run without Secure Boot even if the feature was listed as a requirement. We wish the same could be said for Microsoft’s latest Windows 11.
Some of the many early users of the first Windows 11 Insider Preview build are reporting that they’re unable to install the build and are outright shown a message that their PC can’t run Windows 11. The exact message can be seen in the image below.

Let’s take a step back and find out what Secure Boot really is.
What is Secure Boot?
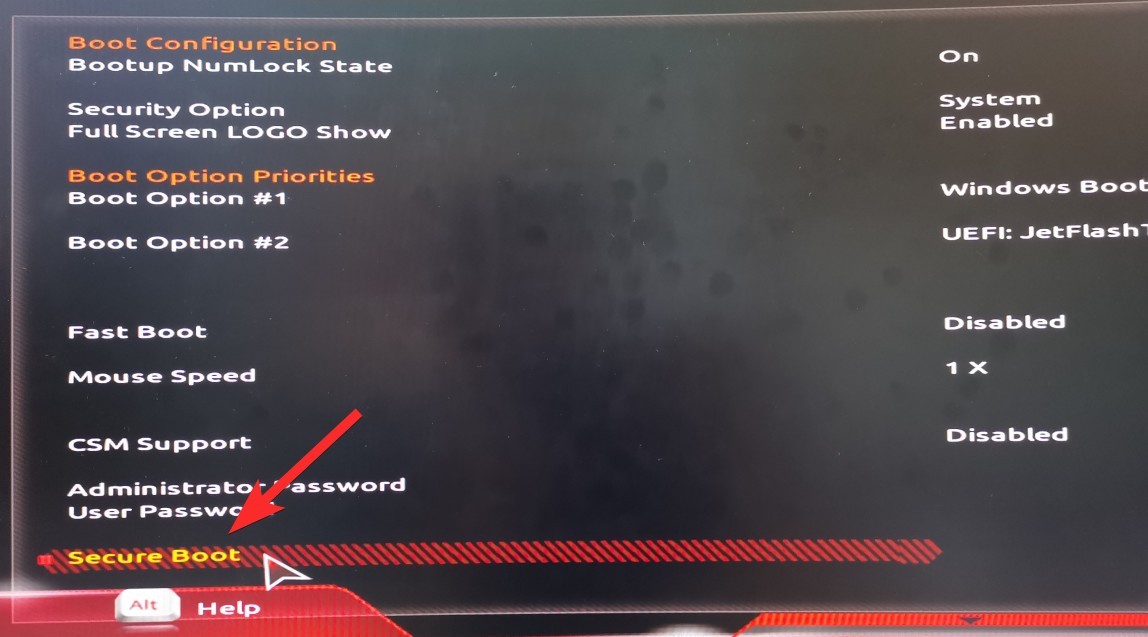
Secure Boot falls under UEFI, short for Unified Extensible Firmware Interface. You can think of UEFI as a software interface that sits between your operating system, firmware, and hardware. UEFI plans to replace BIOS (the interface that we had during the Windows 7 era and before) and it is what comes installed in every modern PC you can purchase right now.
In reality, Secure Boot is a protocol under UEFI 2.3.1 that exists to secure the system boot process by not loading any unsigned UEFI drivers or unsigned operating system boot loaders.
Its only role is to essentially block any piece of code (drivers, bootloaders, or applications) that aren’t signed by the OEMs (Original Equipment Manufacturers) Platform Key.
If the UEFI driver, application, or OS bootloader does have the signed Platform Keys, only then is it permitted to run.
For you and me, it’s just a simple toggle in the UEFI menu that should always be enabled for maximum protection.
But Why is Windows 11 so dead set on requiring Secure Boot?
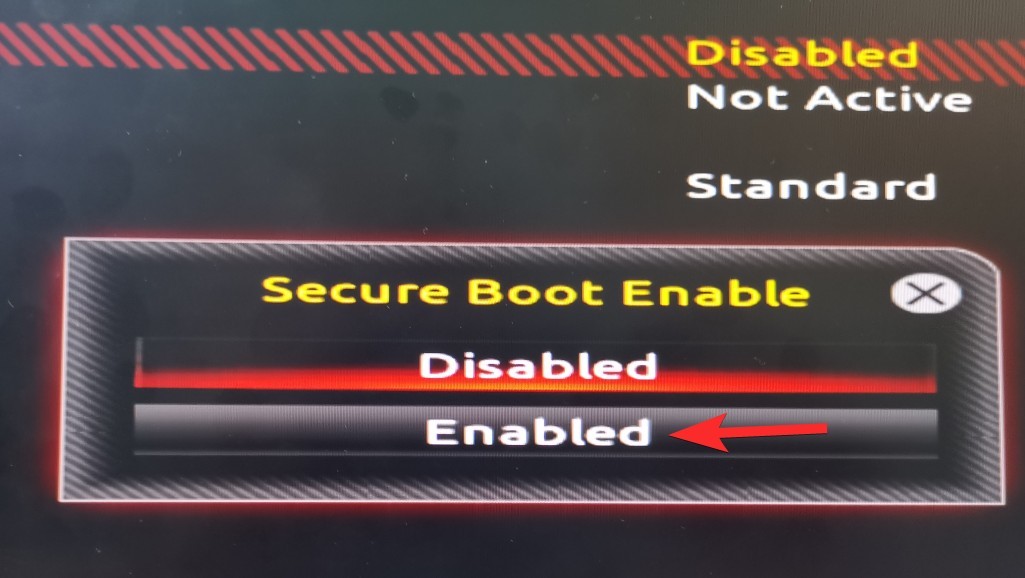
Windows has been trying to enforce Secure Boot ever since the release of Windows 8, and it seems like they won’t take no for an answer as the pros far outweigh the cons.
Microsoft claims that they have built Windows 11 around three key principles: Security, Reliability, and Compatibility. Looking at the additional requirement of Secure Boot and TPM 2.0, it seems that Security has taken the limelight.
According to Microsoft, these hardware requirements are critical to implementing stronger security for your PC, including for the features like Windows Hello, Device Encryption, Virtualization-Based Security (VBS), and HyperVisor-protected Code Integrity (HVCI).
Together, they can help keep your PC safe by reducing malware attacks by 60%.
Still too complex? Let’s make it even simpler.
Think of a scenario where you’ve just downloaded an executable file, say, an installer for a photo editing application. Little did you know that the program you just downloaded, and installed contained a harmful block of code that’s designed to execute on the next system boot.
You finish your task, shut down the PC, and go to bed. You turn back your PC the next day and everything goes haywire.
Your screen gets bombarded with alerts saying “Your car insurance has expired! Click here to renew.” Whatever you do, nothing seems to work. And the result? A completely unusable PC.
Thankfully, modern PCs (think 2017 and later) come with UEFI out-of-the-box, which means that by default Secure Boot is enabled on them.
Now, let’s re-run the same scenario we just mentioned and see what would’ve happened if the PC had Secure Boot enabled.
When you pressed the power button the next morning and unknowingly triggered the malicious code block to execute, Secure Boot takes total control of the boot process, thoroughly checking each and every application, driver, and bootloader that was queued up in the boot queue.
It found out that a harmful block of code exists in the boot queue without a valid Platform Key and hence completely denied its execution.
Yay! No more unwanted popups!
All in all, Secure Boot does a wonderful job of strengthening the security of your operating system while offering a couple of more powerful and advanced features than BIOS.
But there are a couple of downsides to Secure Boot. Some applications, even Linux distros require Secure Boot to be disabled.
How Do I Enable Secure Boot?

Enabling Secure Boot is a fairly straightforward process. One of our amazing writers has already gone over the process in great detail at the link below. Be sure to check it out.
On some systems, you have to disable CSM to unlock the hidden Secure Boot option in your UEFI screen. If your PC is a recent buy, let’s say 2017 or later, then you should be able to enable Secure Boot. If you can’t, do share your PC’s motherboard’s model no. with us in the comments box below.
That’s all.
How to install Windows 11 yourself without the Microsoft Insider program:
- Step 1: Download Windows 11 Insider ISO
- Step 2: Create a Bootable Windows 11 USB Pen Drive with ISO
- Step 3: Install Windows 11 From USB
- Also see: How To Dual Boot Windows 11 with Windows 10




Hmmm
“Secure boot” and “TPM” are in reality nothing more than devices to uniquely identify and track individual computers that going forward starting with windows 11 CAN NOT BE SHUT OR OR DEACTIVATED. The primary job doesn’t have anything what so ever to do with the security of the end user who actually bought and paid for the system. The primary job of this one two punch is simple: implement a permanent, indelible “unique identifier” obviating the need for things like tracking cookies that can in a very real sense allow Microsoft to seize control of what you thought was YOUR computer as it sees fit…
With windows 11 P in PC has forever been taken away from the user/owner and stolen by Microsoft for its own profit and power. Bear in mind that the EULA that microsoft foists on consumers already “allows” Microsoft to literally copy every single action, transaction, and data that is on or passes thru “your” computer and use that data in anyway it sees fit. This just makes it impossible to limit that ongoing daily theft in any way…
The notion that this kind of intrusive hardwired spyware is good for consumers, isn’t just laughable, it is down right contemptible…In point of fact, a very strong and compelling argument can be made that Microsoft in general and its windows 10-11 operating system in particular represents a clear and present danger to the National Security of the United States. Don’t laugh more than a dozen countries came to the conclusion that windows 8-10 did exactly that years ago…You know countries like China, Russia, etc.
Wow… It’s starting to look like Windows 10 might actually be the last version of Windows I use.