For many of us, checking our mail is the first thing we do when we wake up. It’s fairly undeniable that emails are essential to our existence in this day and age. We simply cannot make do without it not just because it’s useful but also because we’re too habituated now.
But this kind of dependency comes with its own set of risks. Emails are a major hotbed for viruses and other types of malware. Hackers have a major preference for using emails as a medium to hack computers and history is fraught with examples of its effectiveness. Like back in 2000, when the ILOVEYOU virus overwrote system and personal files repeatedly after entering one’s computer when they opened an innocent-looking email costing the world approximately $15 million in damages.
Similarly, another vicious virus, Storm Worm, gained major traction in 2006 with a subject line of ‘230 dead as storm batters Europe’. This particular virus was a Trojan horse that infected computers, sometimes turning them into zombies or bots to continue the spread of the virus and send a huge amount of spam mails to other unsuspecting computers. The exact cost of damages from this malware is yet to be discerned.
So the answer to the question is fairly obvious. Yes, your computer can become infected with a virus via email.
How does a computer get infected with an email virus?

The problem begins when you interact with the malicious code that’s present in suspicious email messages. The virus activates when you open an email attachment or click on a link in the message. Viruses are packaged and presented in many different ways. While some of these emails can be easily spotted as malicious based on their shady subject lines, the name of the sender, or several other alarming and suspicious content, there are some that appear spotless and harmless. The messages in such mails have been crafted with care by the hacker in order to make the email message appear as if it has been sent from a trusted sender. Here are a few things you must watch out for:
Phishing attempts
The term ’phishing’ has actually been derived from the word fishing. Set on the entire premise of hackers dangling a fake ‘bait’ or ‘lure’ in the form of a well-written and legitimate-sounding email, in the hope that the user will ‘bite’ like a fish and provide sensitive information such as credit card numbers, account numbers, passwords, usernames, etc.
Many phishing scams create a sense of urgency with messages like ‘Your password will expire in <number of hours/days>’ or that there is ‘Suspicious Activity’ in your account and you need to click on a link to change it immediately. These mails might also appear to be from brands and services (subscriptions) that you actually use. Basically, a lot about phishing attempts is psychological mind games and you need to be very careful to not fall into such traps.
Email attachments
The email attachment is the most common and effective means for a virus to enter your computer. When you download a suspicious attachment, you’re inadvertently introducing the virus to your system, without even giving away any personal information. You should check the file type of any attachment before opening it.
Malware and viruses can be hidden in files of the following file extensions; .ade,.adp, .asf, .bas, .bat, .chm, .cmd, .com, .cpl, .crt, .exe, .hlp, .hta, inf, .ins, .isp, .js, .jse, .lnk, .mdb, .mde, .mov, .msc, .msi, .msp, .mst, .pcd, .pif, .reg, .scr, .sct, .shs, .swf, .url, .vb, .vbe, .vbs, .wsc, .wsf and .wsh.
But remember that even if the attachment looks harmless and familiar like a Microsoft document or a PDF, the virus can be concealed within them in the form of malicious link or code.
Hyperlinks
This is a hyperlink. When you clicked on it, you did not have any idea about where it would lead you. Of course, not everyone is as well-intentioned as we are. Whether it’s a stealthy phishing attempt or a blatantly obvious malicious mail, hyper-links will prove to be just as lethal as attachments, if not worse. Clicking on the link might lead you to a malicious web page or worse, trigger the download of a virus directly.

When you come across a suspicious hyperlink from a brand or service that you’re using, instead of clicking the hyper-link, manually type the link of the official website and visit the relevant page to check for yourself.
Social Engineering
Your eyes, especially, can deceive you and this is where Social Engineering comes into the picture. The hacker investigates their intended victim to gather background information such as potential points of entry and weak security protocols needed to proceed with the attack. Then, they will gain the victim’s trust and create situations for subsequent actions that grant special access and reveal sensitive information.
To avoid falling into a hacker’s phishing scams and real-life baiting, don’t share any passwords or sensitive information with anyone, even if they appear to work in the same organization as you do. A socially engineered event can be convincing enough to tempt you into a trap no matter how careful you are. We have covered the safety aspects later in this article.
Types of virus that can infect computers via email

Viruses tend to evolve, both the ones that attack our bodies as well as the ones that hack our computers. So it should not come as a surprise that the digital viral pandemic is so robust and filled with variety. You need to be careful about what you’re allowing into your computer system because depending on the range of the virus’s damage, this could end up being a super expensive affair for you. Here’s a look at what you need to watch out for.
Worms
Worms have been around much longer than computer viruses, at a time when computers were still massive immobile machines. Not surprisingly, worms made a big comeback in the late 1990s and plagued computers in the form of email attachments. Worms were so contagious that even if one person would open an infected email, the entire company would follow in very little time.
The worm is self-replicating. For example, in the case of the ILOVEYOU virus, it hit nearly every email user in the world, overloaded phone systems (with fraudulently sent texts), brought down television networks, and even disrupted services in real-life. Worms are effective because unlike in the case of conventional viruses, they can spread without end-user action, the worm makes another program do all the dirty work.
Trojan
Trojans have now replaced computer worms as the preferred medium of hacking and have taken hold of current computers more than any other type of malware. It is basically a malicious code/software that can take control of your computer. The virus is designed to damage, disrupt, steal, or in general, inflict some other harmful action on your data or network.
This virus usually arrives via email or are pushed on users when they visit infected websites. The most popular Trojan type is the fake antivirus program that pops up and claims you’re infected, then instructs you to run a program to clean your PC.
Ransomware
Ransomware viruses like WannaCry and Petya are extremely famous for their reach and damage. As the name implies, ransomware is a form of malware that encrypts a victim’s files and will only restore access to the victim upon payment of the ‘ransom’ which will show the victim the instructions for how to pay a fee to get the decryption key. This cost can range from a few hundred dollars to thousands, payable to cybercriminals in Bitcoin. In many ways, ransomware has evolved from Trojan.
One of the most common delivery systems for ransomware is a phishing attachment that arrives in the email of the victim, masquerading as a file they should trust. Once it’s downloaded and opened, the ransomware can takes over the victim’s computer taking over even administrative access. Some ransomware like NotPetya was notorious for exploiting security holes to infect computers without even the need to trick users.
Spyware
When hackers use spyware to log the keystrokes of victims and gain access to passwords or intellectual property, you won’t even see it coming and the chances are that it will be too late by the time you do. Spyware is basically any software that installs itself on your computer and starts covertly monitoring your online behavior without your knowledge or permission, it then relays this data to other parties. In some cases, these may be advertisers or marketing data firms, which is why spyware is sometimes referred to as “adware.” It is installed without user consent by methods such as a drive-by download, a trojan included with a legitimate program, or a deceptive pop-up window.
The presence of a spyware program should serve as a warning that your computer has a vulnerability that needs to be fixed. If you have the right defenses in place, anything super crazy that could possibly occur thanks to spyware will be avoided.
Adware
Adware is not super malicious in the sense that at least your data is not compromised. If you’ve come in contact with adware it is likely to expose you to unwanted, potentially malicious advertising. Common adware programs usually redirect a user’s browser searches to look-alike web pages that contain other product promotions instead.
What to keep safe from virus from email?

Rely on common sense
Staying safe is more about using your head than the right brand of anti-virus. Just don’t risk it in the first place no matter how compelling the email is because it is always too good to be true despite what Hollywood repeatedly attempts to portray. Simply don’t open suspicious/unfamiliar emails, let alone email attachments, and never click on any promising/suspicious hyperlinks anywhere on the web.
Make sure the email is genuine (verify the domain name)
To properly identify the email’s sender, you must look carefully at its domain name in the email address. For example, Facebook emails to you should have Facebook.com after the ‘@’ or ‘.’ (period) . For example, these are fine:
- xyz@facebook.com
- xyz@fbsupport.facebook.com
But emails like this are not:
- xyz@fbsupport-facebook.com (because fbsupport-facebook.com is a different domain than Facebook, thus this email is not from Facebook. Lucky for you, at least support-facebook.com is own by Facebook and it redirects you to their help page.
- xyz@prizes-facebook.com
The best way to find whether the domain in the email is genuine or not, you can open it in your browser. If you got an email from somebody suspicious, then hover over the email to get the sender’s email address. now, select the portion of the email right before and after the last period in the this address.

For exmaple, in the email address above, you have these:
- noreply-in@email.decathlon.in (full sender email address)
- email.decathlon.in (email’s domain)
- decathlon.in (main domain address)
Now, we can try to open the main domain in our browser. That we type decathlon.in in our browser (on mobile/PC) and that should open the genuine website of decathlon. But be sure to not rely on a phishing website that may look like decathlon. So, even better way to confirm the sender address in this case is to search for decathlon on Google, go to their website, go to their support page, and see the domain name there. Does the domain name match the domain name of the email you received? If yes, then the email is safe.
Watch out for the signs
There are always signs like not addressing the recipient of the email by name, the mail not making sense in context to your relationship with the service (when it states that there have been too many login attempts when you haven’t visited the account in quite some time), grammatical errors and really questionable links and attachments. If you look closely enough, you will find yourself wanting to know the source of the mail.
Check the source of the email
Stay on guard for emails that are arriving from unknown sources. In fact, even if the source appears to be familiar but asking you to do something like download an attachment or click a hyperlink, then you need to at least check the name and email id of the sender. There is a lot that you can identify just from the little things.
If you feel you need to authenticate the source of the mail, there is a way to do this. We will be using a promotional mail from Disney+ (not a malicious mail) to explain how it works, you can follow the same method to verify anything that you’re suspicious about.
First, open the mail in your inbox.

Next, click the three-dot menu on the right.
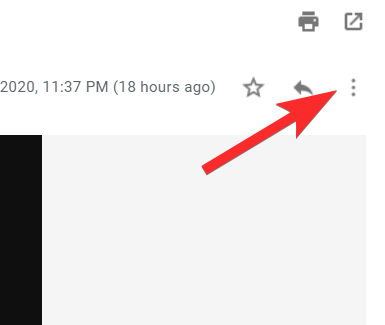
You will now see Show Original in the menu, click on it.
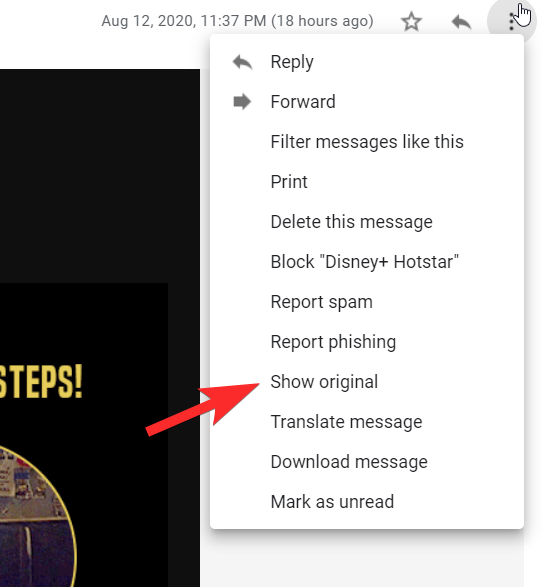
On the Original Message page, the entire HTML code for the mail will be available.

You need to copy the entire code.

Now, go to Google’s MessageHeader application.
Paste the email header that you’d copied in the text box.

Now, verify the information in your email and on the app to check if they match. If there are any discrepancies in the sender data or the nature of the mail, it will show here.

You can use this method to check any mail that you’re suspicious of and report it to Google in case it is.
Multi-factor authentication
When you’re using a multi-factor authentication that involves an extra step of security, two things happen. First, the hacker will not have an easy time breaking in and second, they will lose the motivation to pursue you and move on to an easier target. So besides having a password to access your email, when you add say, even a security question, personal code, or biometric, it can make a world of difference in keeping your organization safe and secure.
Install a reliable anti-virus
The policeman, the security guard, the gatekeeper, however, you want to describe it, an anti-virus is all good, necessary step to take in safeguarding your computer. There is a great variety of options available online and undoubtedly, paying for a yearly subscription will buy you some peace of mind.
Our computers have more value than physical safes these days and unfortunately, the bad guys only know this too well. This is why despite every measure in place, the one thing to remember is that cybercrimes will always loom over our society and the best thing to do is remain vigilant. Make sure your system remains safe and don’t forget to backup your data. Take care and stay safe!