Much ado has been made of Blockchains as of late. With Cryptocurrencies like Bitcoin and Ethereum surging in value, as well as the promise of new blockchain-based technologies like Ethereum’s decentralized network and decentralized apps (dApps) based on it, many wonder what the foundational building blocks of this emerging technology are.
What exactly is it that keeps the blockchain secure and safe against cybercriminals? Well? One of the key components of any blockchain’s integrity is something called one-way hashing. But how does it work, and, more importantly, how does it keep you safe?
What is One-Way Hashing?
One-way hashing is a cryptographic technique that is used to protect data from theft and tampering. In the context of blockchain technology, hashing is what preserves the integrity and immutability of each block in the chain. One way hashing boils down to a three-step process: input (e.g. a password), a hash function (the algorithm used to hash the input), and then the result of the hashing known as the hash value.
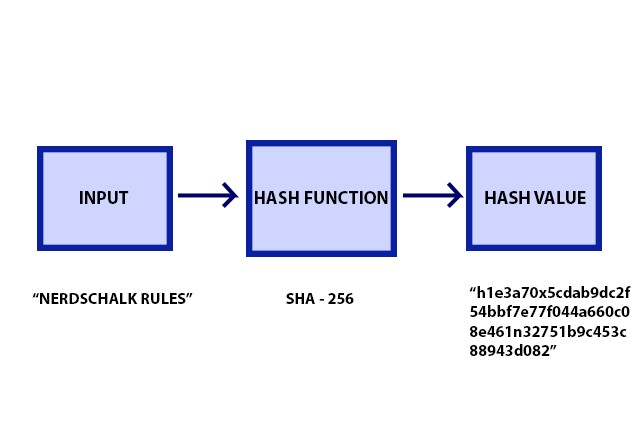
The hash function, in simple terms, scrambles the input to create a set output. The same input will always create the same output, therefore someone can check the veracity of something like a password without ever knowing the actual password. This way a hash value can be stored on a server and use to authenticate logins and other credentials without storing the actual, real data, thus negating the risk of exposure to cybercriminals — even in the event of a data breach!
To help illustrate how hashing works, imagine there exists a magical device known as the Scrambler that changes the words spoken into it into a random assortment of letters and numbers. Nobody knows how the Scrambler does it, only that it is consistent — saying the words “the lazy cat” into the scrambler always produces the string “149den584b3.”
Now imagine you’re trying to enter a secret club that requires a password to enter. The doorman has a list of scrambled passwords. You walk up to the club, put your lips to the voice scrambler and whisper into it “the lazy cat.” Out comes the string “149den584b3.” The doorman checks his list, sees that string on it, and lets you into the club.
You were able to enter the club with your secret password without ever revealing your secret password. Even the doorman cannot use the password because he can never know what the phrase was that, when spoken through the scrambler, produces that string. It could be anything.
Why is One-Way Hashing Secure?

That’s essentially how one-way hashing works. The input is your original password, the voice scrambler is the hash function, and the resultant string is the hash value. A key component to the security of one-way hashing is the fact that it is almost or completely impossible to derive the original input from the hash value. This is because hashing reduces strings of any size into a string of fixed size.
Hearkening back to the hypothetical voice scrambler, this would mean you could speak a sentence of any length into it but the resultant password would always be 11 digits. This way, an attacker has no way of knowing how long or short the original input value is.
On top of that, due to a key feature of hashing known as the Avalanche Effect, even a minor change in the original input will result in a drastically different hash value. For example, changing just one letter in “the lazy cat” to make the “the lazy car” might result in changing the original hash value from “149den584b3” to “58bi5i12l99.”
In reality, hash values are typically much longer than 11 digits. The widely used SHA-256 protocol used as the basis for Bitcoin’s blockchain and many others creates 64-digit hexadecimals like the one shown above. This is considered the current gold standard for encryption, though that is subject to change with the rapid acceleration in computing power
For now, at least, one-way hashing using SHA-256 and other methods remains more than enough to keep you and your data safe.
Still confused? We understand. And we’re here to help. Feel free to reach out to us in the comments below — we’ll get back to you as soon as we can!






